"Greatest Danger To National Security" - Ed Snowden Exposes The 'Insecurity' Industry
Authored by Edward Snowden via "Continuing Ed" substack,
The greatest danger to national security has become the companies that claim to protect it...
1.
The first thing I do when I get a new phone is take it apart. I don’t do this to satisfy a tinkerer’s urge, or out of political principle, but simply because it is unsafe to operate. Fixing the hardware, which is to say surgically removing the two or three tiny microphones hidden inside, is only the first step of an arduous process, and yet even after days of these DIY security improvements, my smartphone will remain the most dangerous item I possess.
The microphones inside my actual phone, prepped for surgery
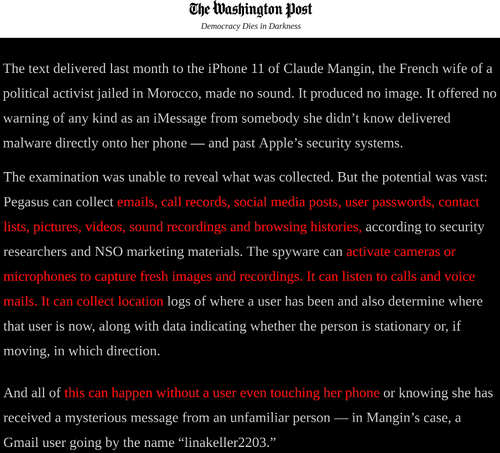
Prior to this week’s Pegasus Project, a global reporting effort by major newspapers to expose the fatal consequences of the NSO Group—the new private-sector face of an out-of-control Insecurity Industry—most smartphone manufacturers along with much of the world press collectively rolled their eyes at me whenever I publicly identified a fresh-out-of-the-box iPhone as a potentially lethal threat.
Despite years of reporting that implicated the NSO Group’s for-profit hacking of phones in the deaths and detentions of journalists and human rights defenders; despite years of reporting that smartphone operating systems were riddled with catastrophic security flaws (a circumstance aggravated by their code having been written in aging programming languages that have long been regarded as unsafe); and despite years of reporting that even when everything works as intended, the mobile ecosystem is a dystopian hellscape of end-user monitoring and outright end-user manipulation, it is still hard for many people to accept that something that feels good may not in fact be good. Over the last eight years I’ve often felt like someone trying to convince their one friend who refuses to grow up to quit smoking and cut back on the booze—meanwhile, the magazine ads still say “Nine of Ten Doctors Smoke iPhones!” and “Unsecured Mobile Browsing is Refreshing!”
In my infinite optimism, however, I can’t help but regard the arrival of the Pegasus Project as a turning-point—a well-researched, exhaustively-sourced, and frankly crazy-making story about a “winged” “Trojan Horse” infection named “Pegasus” that basically turns the phone in your pocket into an all-powerful tracking device that can be turned on or off, remotely, unbeknownst to you, the pocket’s owner.
Here is how the Washington Post describes it:
In short, the phone in your hand exists in a state of perpetual insecurity, open to infection by anyone willing to put money in the hand of this new Insecurity Industry. The entirety of this Industry’s business involves cooking up new kinds of infections that will bypass the very latest digital vaccines—AKA security updates—and then selling them to countries that occupy the red-hot intersection of a Venn Diagram between “desperately craves the tools of oppression” and “sorely lacks the sophistication to produce them domestically.”
An Industry like this, whose sole purpose is the production of vulnerability, should be dismantled.
2.
Even if we woke up tomorrow and the NSO Group and all of its private-sector ilk had been wiped out by the eruption of a particularly public-minded volcano, it wouldn’t change the fact that we’re in the midst of the greatest crisis of computer security in computer history. The people creating the software behind every device of any significance—the people who help to make Apple, Google, Microsoft, an amalgamation of miserly chipmakers who want to sell things, not fix things, and the well-intentioned Linux developers who want to fix things, not sell things—are all happy to write code in programming languages that we know are unsafe, because, well, that’s what they’ve always done, and modernization requires a significant effort, not to mention significant expenditures. The vast majority of vulnerabilities that are later discovered and exploited by the Insecurity Industry are introduced, for technical reasons related to how a computer keeps track of what it’s supposed to be doing, at the exact time the code is written, which makes choosing a safer language a crucial protection... and yet it’s one that few ever undertake.
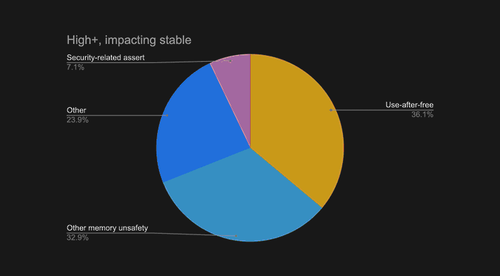
Google said 70% of serious bugs in its Chrome Browser are related to memory safety. These can be reduced by using safer programming languages.
If you want to see change, you need to incentivize change. For example, if you want to see Microsoft have a heart attack, talk about the idea of defining legal liability for bad code in a commercial product. If you want to give Facebook nightmares, talk about the idea of making it legally liable for any and all leaks of our personal records that a jury can be persuaded were unnecessarily collected. Imagine how quickly Mark Zuckerberg would start smashing the delete key.
Where there is no liability, there is no accountability... and this brings us to the State.
3.
State-sponsored hacking has become such a regular competition that it should have its own Olympic category in Tokyo. Each country denounces the others’ efforts as a crime, while refusing to admit culpability for its own infractions. How, then, can we claim to be surprised when Jamaica shows up with its own bobsled team? Or when a private company calling itself “Jamaica” shows up and claims the same right to “cool runnings” as a nation-state?
If hacking is not illegal when we do it, then it will not be illegal when they do it—and “they” is increasingly becoming the private sector. It’s a basic principle of capitalism: it’s just business. If everyone else is doing it, why not me?
This is the superficially logical reasoning that has produced pretty much every proliferation problem in the history of arms control, and the same mutually assured destruction implied by a nuclear conflict is all-but guaranteed in a digital one, due to the network’s interconnectivity, and homogeneity.
Recall our earlier topic of the NSO Group’s Pegasus, which especially but not exclusively targets iPhones. While iPhones are more private by default and, occasionally, better-engineered from a security perspective than Google’s Android operating system, they also constitute a monoculture: if you find a way to infect one of them, you can (probably) infect all of them, a problem exacerbated by Apple’s black-box refusal to permit customers to make any meaningful modifications to the way iOS devices operate. When you combine this monoculture and black-boxing with Apple’s nearly universal popularity among the global elite, the reasons for the NSO Group’s iPhone fixation become apparent.
Governments must come to understand that permitting—much less subsidizing—the existence of the NSO Group and its malevolent peers does not serve their interests, regardless of where the client, or the client-state, is situated along the authoritarian axis: the last President of the United States spent all of his time in office when he wasn’t playing golf tweeting from an iPhone, and I would wager that half of the most senior officials and their associates in every other country were reading those tweets on their iPhones (maybe on the golf course).
Whether we like it or not, adversaries and allies share a common environment, and with each passing day, we become increasingly dependent on devices that run a common code.
The idea that the great powers of our era—America, China, Russia, even Israel—are interested in, say, Azerbaijian attaining strategic parity in intelligence-gathering is, of course, profoundly mistaken. These governments have simply failed to grasp the threat, because the capability-gap hasn’t vanished—yet.
4.
In technology as in public health, to protect anyone, we must protect everyone. The first step in this direction—at least the first digital step—must be to ban the commercial trade in intrusion software. We do not permit a market in biological infections-as-a-service, and the same must be true for digital infections. Eliminating the profit motive reduces the risks of proliferation while protecting progress, leaving room for publicly-minded research and inherently governmental work.
While removing intrusion software from the commercial market doesn’t also take it away from states, it does ensure that reckless drug dealers and sex-criminal Hollywood producers who can dig a few million out of their couch cushions won’t be able to infect any or every iPhone on the planet, endangering the latte-class’ shiny slabs of status.
Such a moratorium, however, is mere triage: it only buys us time. Following a ban, the next step is liability. It is crucial to understand that neither the scale of the NSO Group’s business, nor the consequences it has inflicted on global society, would have been possible without access to global capital from amoral firms like Novalpina Capital (Europe) and Francisco Partners (US). The slogan is simple: if companies are not divested, the owners should be arrested. The exclusive product of this industry is intentional, foreseeable harm, and these companies are witting accomplices. Further, when, a business is discovered to be engaging in such activities at the direction of a state, liability should move beyond more pedestrian civil and criminal codes to invoke a coordinated international response.
Diplomacy by other means
5.
Imagine you’re the Washington Post’s Editorial Board (first you’ll have to get rid of your spine). Imagine having your columnist murdered and responding with a whispered appeal to the architects of that murder that next time they should just fill out a bit more paperwork. Frankly, the Post’s response to the NSO scandal is so embarrassingly weak that it is a scandal in itself: how many of their writers need to die for them to be persuaded that process is not a substitute for prohibition?
Saudi Arabia, using “Pegasus,” hacked the phones of Jamal Khashoggi’s ex-wife, and of his fiancée, and used the information gleaned to prepare for his monstrous killing and its subsequent cover-up.
But Khashoggi is merely the most prominent of Pegasus’ victims — due to the cold-blooded and grisly nature of his murder. The NSO Group’s “product” (read: “criminal service”) has been used to spy on countless other journalists, judges, and even teachers. On opposition candidates, and on targets’ spouses and children, their doctors, their lawyers, and even their priests. This is what people who think a ban is “too extreme” always miss: this Industry sells the opportunity to gun down reporters you don’t like at the car wash.
If we don’t do anything to stop the sale of this technology, it’s not just going to be 50,000 targets: It’s going to be 50 million targets, and it’s going to happen much more quickly than any of us expect.
This will be the future: a world of people too busy playing with their phones to even notice that someone else controls them.
https://ift.tt/3BMKgHN
from ZeroHedge News https://ift.tt/3BMKgHN
via IFTTT



0 comments
Post a Comment